Comprehensive Guide To Bearer Token Generation: Best Practices And Insights
Bearer token generation is not just a technical necessity but also a strategic advantage for businesses relying on APIs. These tokens are compact, self-contained, and easy to implement, making them a popular choice for developers. However, understanding the nuances of bearer token generation is essential to ensure their effective and secure use. From OAuth 2.0 protocols to JWT (JSON Web Tokens), the mechanisms behind bearer token generation are diverse and adaptable to various use cases. As technology evolves, so do the methods and best practices surrounding bearer token generation. In this article, we will delve into the intricacies of bearer token generation, exploring its mechanisms, benefits, and potential challenges. We’ll also cover the steps to generate these tokens securely, highlight common mistakes to avoid, and provide actionable insights for developers and organizations. Whether you're new to the concept or looking to refine your understanding, this guide will equip you with the knowledge to implement bearer token generation effectively in your projects.
Table of Contents
- What Are Bearer Tokens and How Do They Work?
- How Can You Securely Generate Bearer Tokens?
- What Are the Common Mistakes in Bearer Token Generation?
- Why Is Bearer Token Generation Important for API Security?
- What Are the Best Practices for Managing Bearer Tokens?
- How Does Bearer Token Generation Integrate with OAuth 2.0?
- What Are the Alternatives to Bearer Tokens?
- How Can You Troubleshoot Bearer Token Issues?
What Are Bearer Tokens and How Do They Work?
Bearer tokens are a type of access token used in authentication protocols to grant access to resources. The term "bearer" implies that anyone possessing the token can access the associated resources, making it crucial to handle these tokens securely. Typically, bearer tokens are generated by an authentication server after verifying a user's credentials. Once issued, the token is included in the HTTP Authorization header of API requests, allowing the server to validate the user's identity without requiring repeated login credentials.
How Are Bearer Tokens Generated?
The process of bearer token generation involves several steps. First, the client application sends a request to the authentication server with the user's credentials, such as a username and password. The server verifies these credentials and, if valid, generates a unique token. This token is often encrypted and contains metadata, such as the user's identity, expiration time, and permissions. The token is then sent back to the client, which includes it in subsequent API requests.
Read also:Who Is Josh Dawsey Discovering The Man Behind The Name
What Makes Bearer Tokens Secure?
Bearer tokens are designed to be secure, but their safety largely depends on proper implementation. These tokens are typically short-lived, reducing the risk of misuse if intercepted. Additionally, they are transmitted over secure channels, such as HTTPS, to prevent eavesdropping. Developers can further enhance security by implementing token revocation mechanisms and monitoring for suspicious activity.
How Can You Securely Generate Bearer Tokens?
Generating bearer tokens securely is a multi-step process that requires careful attention to detail. The first step is to use a robust authentication framework, such as OAuth 2.0 or OpenID Connect, which provides standardized methods for token generation. These frameworks ensure that tokens are created using secure algorithms and include essential metadata, such as expiration times and scopes.
Steps to Generate Bearer Tokens
- Authenticate the User: Verify the user's identity using credentials like a username and password.
- Generate the Token: Use a secure algorithm to create a unique token. This often involves hashing and encryption techniques.
- Set Expiration: Define a short lifespan for the token to minimize the risk of misuse.
- Store Securely: Ensure the token is stored securely on the client side, such as in memory or a secure storage mechanism.
- Transmit Over HTTPS: Always send the token over encrypted channels to prevent interception.
What Are the Key Security Considerations?
When generating bearer tokens, it's essential to consider potential vulnerabilities. For example, tokens should never be stored in cookies or local storage, as these can be accessed by malicious scripts. Additionally, developers should implement token revocation mechanisms to invalidate tokens in case of suspicious activity. Regularly rotating encryption keys and monitoring token usage can further enhance security.
What Are the Common Mistakes in Bearer Token Generation?
Despite their benefits, bearer tokens are often misused or improperly implemented, leading to security vulnerabilities. Understanding these common mistakes can help developers avoid pitfalls and ensure secure token generation.
1. Storing Tokens Insecurely
One of the most frequent mistakes is storing bearer tokens in insecure locations, such as local storage or cookies. These locations are accessible to JavaScript, making them vulnerable to cross-site scripting (XSS) attacks. Instead, tokens should be stored in memory or secure storage mechanisms.
2. Using Long-Lived Tokens
Another common mistake is issuing tokens with long expiration times. While this may seem convenient, it increases the risk of misuse if the token is intercepted. Short-lived tokens, combined with refresh tokens, provide a better balance between security and usability.
Read also:Discover The Beauty Of Haulover Beach A Hidden Gem In Miami
3. Neglecting Token Revocation
Many developers overlook the importance of token revocation. Without a mechanism to invalidate tokens, compromised tokens can remain active indefinitely. Implementing token revocation and monitoring usage patterns can mitigate this risk.
Why Is Bearer Token Generation Important for API Security?
In the context of API security, bearer token generation plays a pivotal role in protecting sensitive data and ensuring authorized access. APIs are the backbone of modern applications, enabling seamless communication between different systems. However, they are also prime targets for cyberattacks, making secure authentication methods like bearer tokens essential.
How Do Bearer Tokens Enhance API Security?
Bearer tokens provide a stateless and scalable way to authenticate API requests. Unlike traditional session-based authentication, which requires storing session data on the server, bearer tokens are self-contained. This reduces server overhead and allows APIs to scale more efficiently. Additionally, bearer tokens can be easily revoked or expired, providing an extra layer of security.
What Are the Benefits of Stateless Authentication?
- Scalability: Stateless tokens eliminate the need for server-side session storage, enabling APIs to handle more requests.
- Flexibility: Tokens can be used across multiple platforms and devices without requiring additional infrastructure.
- Security: By including metadata like expiration times, tokens reduce the risk of unauthorized access.
What Are the Best Practices for Managing Bearer Tokens?
Managing bearer tokens effectively is as important as generating them securely. Proper token management ensures that tokens remain valid only for their intended use and are promptly revoked if compromised. Below are some best practices for managing bearer tokens.
1. Use Short-Lived Tokens
Short-lived tokens minimize the risk of misuse if intercepted. By combining them with refresh tokens, developers can maintain a seamless user experience while ensuring security.
2. Implement Token Revocation
Token revocation mechanisms allow developers to invalidate tokens in case of suspicious activity or user logout. This ensures that compromised tokens cannot be reused.
3. Monitor Token Usage
Regularly monitoring token usage patterns can help detect anomalies, such as unexpected access locations or high-frequency requests. This proactive approach can prevent potential breaches.
How Does Bearer Token Generation Integrate with OAuth 2.0?
OAuth 2.0 is one of the most widely used frameworks for bearer token generation. It provides a standardized way to issue and manage tokens, making it easier for developers to implement secure authentication. Understanding how bearer token generation integrates with OAuth 2.0 is essential for building robust authentication systems.
What Is the Role of OAuth 2.0 in Token Generation?
OAuth 2.0 defines the process for issuing access tokens, including bearer tokens. It specifies how clients can request tokens from an authorization server and how these tokens should be used to access protected resources. The framework also supports various grant types, such as authorization code and client credentials, catering to different use cases.
How Does OAuth 2.0 Enhance Token Security?
OAuth 2.0 enhances token security by enforcing strict validation rules and supporting short-lived tokens. It also provides mechanisms for token revocation and refresh, ensuring that tokens remain secure throughout their lifecycle.
What Are the Alternatives to Bearer Tokens?
While bearer tokens are widely used, they are not the only option for securing API communications. Depending on the use case, developers may consider alternatives like API keys, session-based authentication, or mutual TLS. Each method has its own advantages and limitations, making it essential to choose the right approach for your application.
1. API Keys
API keys are simple and easy to implement but lack the flexibility and security of bearer tokens. They are often used for basic authentication but are not suitable for complex systems.
2. Mutual TLS
Mutual TLS provides a high level of security by authenticating both the client and the server. However, it requires significant infrastructure and is more complex to implement than bearer tokens.
How Can You Troubleshoot Bearer Token Issues?
Despite their advantages, bearer tokens can sometimes lead to issues like invalid tokens, expired tokens, or unauthorized access errors. Troubleshooting these issues requires a systematic approach to identify and resolve the root cause.
1. Check Token Expiration
Expired tokens are a common cause of authentication failures. Ensure that tokens are refreshed before they expire to avoid interruptions.
2. Verify Token Scope
Tokens may fail if they lack the necessary permissions or scopes. Review the token's scope to ensure it aligns with the required access level.
3. Inspect Server Logs
Server logs can provide valuable insights into token-related issues. Look for error messages or patterns that indicate potential problems.
Frequently Asked Questions
What Is Bearer Token Generation?
Bearer token generation is the process of creating secure access tokens used for authenticating API requests. These tokens are generated by an authentication server and included in the HTTP Authorization header to grant access to protected resources.
How Long Should a Bearer Token Last?
A bearer token should ideally last only a few minutes to an hour. Short-lived tokens reduce the risk of misuse if intercepted. Refresh tokens can be used to issue new tokens without requiring the user to log in again.
Can Bearer Tokens Be Used for Mobile Applications?
Yes, bearer tokens are commonly used in mobile applications to authenticate API requests. They provide a secure and scalable way to manage user sessions without storing sensitive credentials on the device.
For more information on API security, you can refer to OAuth 2.0's official documentation.
Conclusion
Bearing token generation is a cornerstone of modern API security, offering a secure and scalable way to authenticate users and applications. By understanding the mechanisms, best practices, and potential challenges associated with bearer tokens, developers can implement robust authentication systems that protect sensitive data and ensure authorized access. Whether you're new to bearer tokens or looking to refine your approach, this guide provides the insights and tools needed to succeed in today's digital landscape.
Fun Bits Interactive: Exploring The Joy Of Engaging Content
Charlotte Sullivan Feet: The Complete Guide To Her Life, Career, And Unique Style
Who Is Effi Lotto Himself? A Comprehensive Look At His Life And Achievements
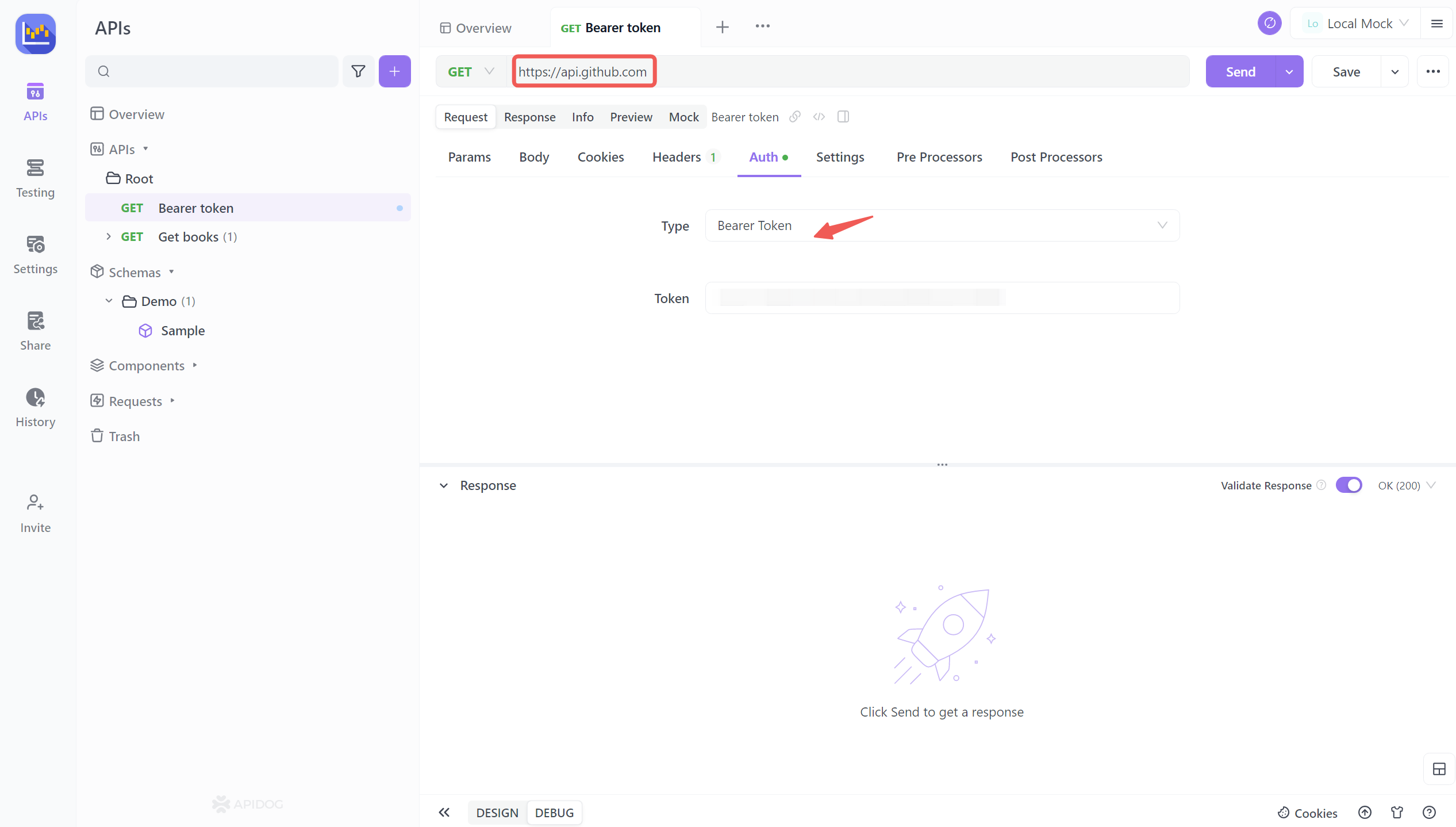
How to Add Bearer Token Authorization in Postman
How to Add Bearer Token Authorization in Postman